Computational indistinguishability
In computational complexity, if 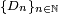 and
and 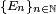 are two distribution ensembles indexed by a security parameter n (which usually refers to the length of the input), then we say they are computationally indistinguishable if for any non-uniform probabilistic polynomial time algorithm A, the following quantity is a negligible function in n:
are two distribution ensembles indexed by a security parameter n (which usually refers to the length of the input), then we say they are computationally indistinguishable if for any non-uniform probabilistic polynomial time algorithm A, the following quantity is a negligible function in n:
denoted 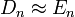 .[1] In other words, every efficient algorithm A's behavior does not significantly change when given samples according to Dn or En in the limit as
.[1] In other words, every efficient algorithm A's behavior does not significantly change when given samples according to Dn or En in the limit as 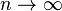 . Another interpretation of computational indistinguishability, is that polynomial-time algorithms actively trying to distinguish between the two ensembles cannot do so: That any such algorithm will only perform negligibly better than if one were to just guess.
. Another interpretation of computational indistinguishability, is that polynomial-time algorithms actively trying to distinguish between the two ensembles cannot do so: That any such algorithm will only perform negligibly better than if one were to just guess.
Implicit in the definition is the condition that the algorithm, 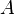 , must decide based on a single sample from one of the distributions. One might conceive of a situation in which the algorithm trying to distinguish between two distributions, could access as many samples as it needed. Hence two ensembles that cannot be distinguished by polynomial-time algorithms looking at multiple samples are deemed indistinguishable by polynomial-time sampling.[2]:107 If the polynomial-time algorithm can generate samples in polynomial time, or has access to a random oracle that generates samples for it, then indistinguishability by polynomial-time sampling is equivalent to computational indistinguishability.[2]:108
, must decide based on a single sample from one of the distributions. One might conceive of a situation in which the algorithm trying to distinguish between two distributions, could access as many samples as it needed. Hence two ensembles that cannot be distinguished by polynomial-time algorithms looking at multiple samples are deemed indistinguishable by polynomial-time sampling.[2]:107 If the polynomial-time algorithm can generate samples in polynomial time, or has access to a random oracle that generates samples for it, then indistinguishability by polynomial-time sampling is equivalent to computational indistinguishability.[2]:108
References
- ↑ Lecture 4 - Computational Indistinguishability, Pseudorandom Generators
- 1 2 Goldreich, O. (2003). Foundations of cryptography. Cambridge, UK: Cambridge University Press.
- Donald Beaver and Silvio Micali and Phillip Rogaway, The Round Complexity of Secure Protocols (Extended Abstract), 1990, pp. 503–513
- Shafi Goldwasser and Silvio Micali. Probabilistic Encryption. JCSS, 28(2):270–299, 1984
- Oded Goldreich. Foundations of Cryptography: Volume 2 – Basic Applications. Cambridge University Press, 2004.
- Jonathan Katz, Yehuda Lindell, "Introduction to Modern Cryptography: Principles and Protocols," Chapman & Hall/CRC, 2007
External links
This article incorporates material from computationally indistinguishable on PlanetMath, which is licensed under the Creative Commons Attribution/Share-Alike License.
![\delta(n) = \left| \Pr_{x \gets D_n}[ A(x) = 1] - \Pr_{x \gets E_n}[ A(x) = 1] \right|.](../I/m/9ea8766080a6ffd516258bc806af3eaa.png)